At SOLUS AI, we are deeply committed to safeguarding our customer’s privacy, viewing it as both an ethical imperative and a compliance requirement. We utilise advanced technologies and stringent security measures to protect sensitive customer data, fostering transparency and control.
We are pleased to announce that SOLUS AI has successfully achieved SOC 2 compliance. This significant milestone reflects our unwavering commitment to the security, availability, and confidentiality of the data entrusted to us by our customers.
SOC 2 compliance underscores our dedication to maintaining robust controls and stringent security measures in our operations, ensuring that our clients can have full confidence in the protection of their data. We believe this achievement further solidifies our position as a trusted partner in the realm of artificial intelligence and data analytics.
What is SOC 2 compliance?
SOC 2, which stands for Service Organization Control 2, is a framework for assessing and ensuring the security, availability, processing integrity, confidentiality, and privacy of customer data in service organisations.
It is a set of standards and guidelines developed by the American Institute of Certified Public Accountants (AICPA) to evaluate how well a company manages and protects customer data. SOC 2 compliance involves a thorough audit and assessment of an organisation’s internal controls and processes related to data security and privacy.
Achieving SOC 2 compliance demonstrates a company’s commitment to data security and privacy, which can be crucial for businesses that handle sensitive customer information, such as cloud service providers, data canters, and other service organisations. It helps build trust with customers, partners, and stakeholders by showing that the organisation has implemented strong controls to protect data from unauthorised access, disclosure, or breaches.
SOLUS is committing to protecting data with SOC 2 certification.
We are aligning ourselves with following the five trust service principles. These principles are designed to assess an organisation’s ability to protect customer data and ensure the reliability and security of its systems and services.
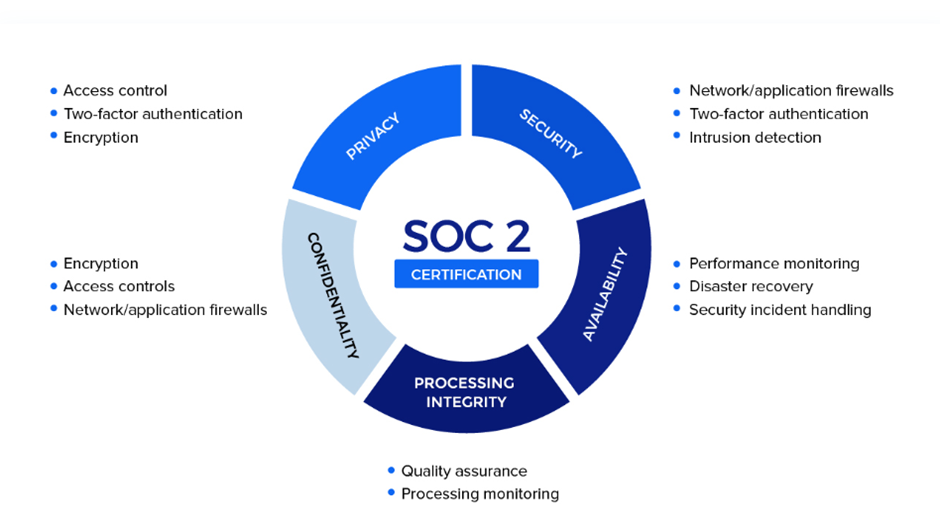
1. Security
The Security principle assesses the effectiveness of an organisation’s controls and measures to protect against unauthorised access, both physical and logical. This includes safeguarding data, equipment, and facilities from threats and vulnerabilities.
2. Availability
The Availability principle evaluates the organisation’s ability to ensure that its systems and services are available and operational when needed to meet its commitments to customers. This principle focuses on minimising downtime and disruptions.
3. Processing integrity
The Processing Integrity principle assesses whether the organisation’s systems and processes are accurate, complete, and reliable in delivering the intended results. It ensures that data is processed correctly and that errors are appropriately addressed.
4. Confidentiality
The Confidentiality principle evaluates the controls and measures in place to protect sensitive information from unauthorised access and disclosure. It includes assessing how the organisation classifies and restricts access to confidential data.
5. Privacy
The Privacy principle assesses the organization’s controls and practices related to the collection, use, retention, and disposal of personal information in accordance with its privacy policies and compliance obligations. It focuses on protecting individuals’ privacy rights.
What does this mean for our customers?
We at SOLUS AI are taking this step to signify our commitment to ensuring the privacy and security of customer information. We recognize the importance of instilling confidence in our customers regarding their data, which is why we are delighted to achieve this certification.
- We utilise an automated GRC platform, guided by our third-party compliance vendor, to effectively manage compliance with all three standards.
- Our security posture undergoes regular assessments and adjustments to align with these standards.
- We’ve centralised all compliance-related documents and tasks for SOC 2 on the platform.
- Our organisation has established and enforces Information Security policies to adhere to these protocols.
- We’ve integrated information security training as a mandatory component of the onboarding process for new team members.
- We’ve implemented a proven framework to identify and address potential issues in real time, ensuring proactive mitigation efforts.
This commitment also signifies that we are actively safeguarding any data under our care. As our valued customers, you can have peace of mind, knowing that your data is securely handled and protected.


